Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

The growing complexity of software licensing has led many users to encounter various challenges in securing legitimate activation codes for their software. As the market becomes increasingly saturated with offers that seem too good to be true, user experiences often reveal a striking trend: the allure of suspicious pricing can lead to costly consequences. Understanding how to discern authentic from counterfeit codes is crucial for anyone seeking reliable software solutions.
One of the primary indicators of questionable offers lies within the credibility of resellers. Evaluating the reputation of vendors and their history of customer feedback is vital. Users should conduct thorough research, examining reviews and ratings, to gauge whether a reseller is trustworthy. This diligence can help in avoiding common pitfalls associated with purchasing from dubious sources.
Additionally, focusing on identifying scams requires awareness of the signs and strategies that fraudsters commonly deploy. Techniques such as price undercutting and pressure tactics are frequently used to manipulate unsuspecting buyers. Employing secure payment methods further shields consumers from potential fraud, ensuring that financial transactions are safe and legitimate. By following these guidelines, individuals can confidently navigate the complexities of software activation while safeguarding their investments.
When assessing the legitimacy of a software activation code, examining its format and length is critical. Genuine codes typically adhere to a specific structure, which can serve as a preliminary check.
Most authentic activation codes consist of five groups of five alphanumeric characters each, formatted as XXXXX-XXXXX-XXXXX-XXXXX-XXXXX. Any deviation from this structure may raise doubts about its authenticity.
Additionally, consider the pricing of a product when evaluating authenticity. If the price is significantly lower than the market average, it may indicate that the source is not reliable. Always verify the credibility of the reseller to ensure you are purchasing from a trustworthy vendor.
Secure payment options should also be a point of focus. Reliable sellers often provide payment methods that offer buyer protection, minimizing risks associated with fraudulent transactions.
User experiences can provide valuable insights into the reliability of a vendor. Look for reviews and feedback from previous customers to gauge the service quality and product validity. A consistent pattern of negative experiences may signal potential issues.
Lastly, a clear return policy can enhance the credibility of a seller. If a vendor offers a straightforward refund option, it can indicate that they stand behind the authenticity of their products. Always check for this assurance before making a purchase.
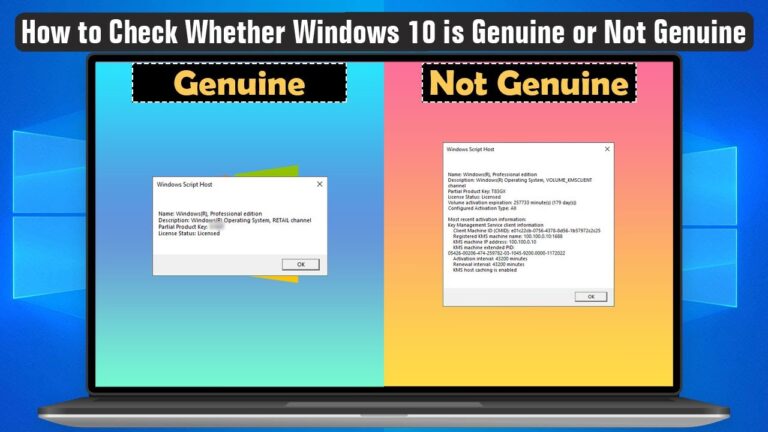
The Genuine Advantage Tool from Microsoft serves as an essential resource for users in verifying the authenticity of their software licenses. This application provides a straightforward way to determine whether your installed operating system is legitimate or not.
To begin using the tool, visit the official Microsoft website and navigate to the download section. This software will scan your system and check the validity of your license against Microsoft’s database. It is highly recommended to download the tool only from the official source to avoid potential scams or security risks that could arise from third-party downloads.
When purchasing software, it’s crucial to assess the credibility of the reseller. Research their reputation through user experiences and reviews to ensure that you are dealing with a trustworthy seller. Look for clear and easily accessible details about their return policy; this can safeguard your investment should you encounter any issues.
In addition, always opt for secure payment methods when buying software online. Such practices protect your financial information and contribute to a more secure transaction.
By using the Genuine Advantage Tool and following these best practices for purchasing software, you can significantly reduce the risk of acquiring untrustworthy software licenses and enhance your overall digital security.
For more information, you can visit Microsoft’s official site: Microsoft.
Engaging in the activation process can serve as a reliable method to ascertain the legitimacy of a software code. Here are some steps and factors to consider:
Incorporating these strategies into your purchase process will enhance your chances of acquiring a legitimate software access code. Always prioritize diligence when making digital purchases.
Before making a purchase, it is crucial to gather information regarding the credibility of the retailer offering the software. Evaluating their standing can help avoid potential issues with your transaction. Here are some key factors to consider:
By thoroughly investigating these aspects, you can make more informed purchasing decisions and minimize the risk of acquiring non-genuine software. Always prioritize reputable sources to ensure a positive buying experience.
Spotting counterfeit software can save users from potential headaches and security threats. Here are some common indicators that may suggest the authenticity of a software license is questionable.
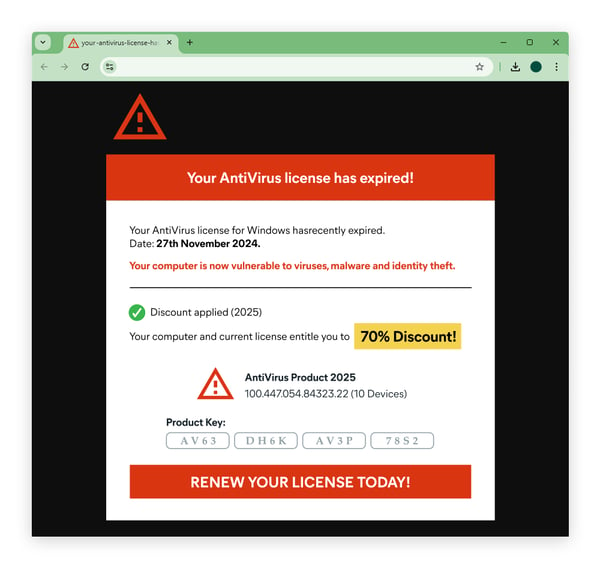
One of the first signs to watch for is unusually low pricing. If the offer seems too good to be true, it likely is. Legitimate licenses typically have a set price based on the publisher’s guidelines. Be wary of discounts that seem excessive compared to established retail offerings.
Researching user reviews can provide valuable insights. Genuine feedback often reveals patterns regarding the reliability of the software. Look out for:
The reliability of the source should not be overlooked. Always opt for reputable sellers with positive track records. Here are factors to consider:
Pay attention to the payment methods offered by the seller. Trustworthy vendors will typically use secure options such as:
Finally, stay alert for common scam tactics, including:
| Signs of Counterfeit Software | Indicators |
|---|---|
| Suspicious Pricing | Prices significantly lower than average |
| User Experiences | Negative reviews and feedback |
| Reseller Credibility | Lack of established reputation |
| Secure Payment Methods | Limited or insecure payment options |
| Identifying Scams | Unsolicited offers and pressure tactics |
By keeping these factors in mind, users can make informed choices and minimize the risk of acquiring counterfeit software licenses.
Evaluating customer feedback is an essential step in ensuring the authenticity of software licenses. Here are some key aspects to consider:
By carefully analyzing customer feedback and considering these factors, individuals can make informed choices when purchasing licenses and avoid potential pitfalls associated with illegitimate sellers.
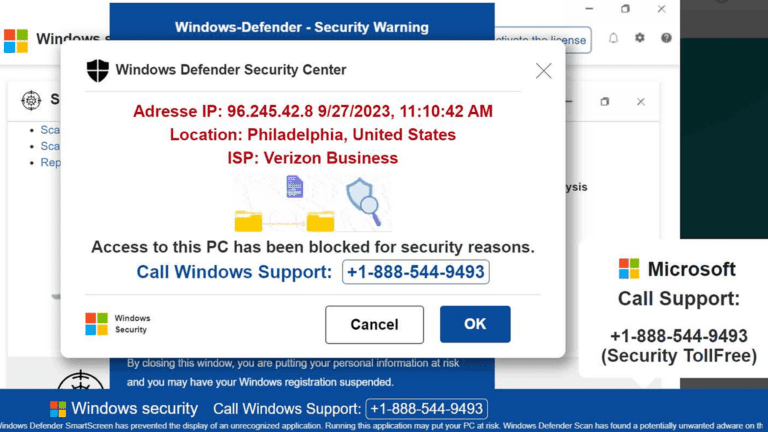
The use of unauthorized software comes with significant dangers that can affect both personal and financial safety. While the allure of free or low-cost alternatives may seem tempting, the hidden costs can far outweigh the initial savings.
Firstly, many individuals face the threat of malware. Pirated versions often contain harmful software that can compromise personal data, including banking information, leading to considerable financial loss. Secure payment methods do not offer protection against transactions involving infected software.
Additionally, suspicious pricing should raise red flags. If a software license is offered at an unusually low price, it may indicate that it is not genuine. Always research reseller credibility to ensure the legitimacy of the product being sold.
Furthermore, relying on unauthorized products can lead to a lack of support and updates from the legitimate vendors. Users often share their experiences online, revealing that once issues arise with pirated software, resolving them becomes extremely complicated, if not impossible.
Identifying scams related to counterfeit software requires vigilance. Look for clear indicators such as a lack of a proper return policy or inadequate contact information for sellers. By staying informed and critical of offers that appear too good to be true, individuals can protect themselves from phishing schemes and other cyber threats.
For more detailed insights on the dangers of pirated software, visit Microsoft’s official anti-piracy page.