Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

Managing the digital environment on a less noisy device involves understanding the unique processes necessary for efficient operation. This setup is critical for unleashing the full potential of your gadget, especially under atypical user conditions, where silence is golden. Leveraging a keyverified approach not only simplifies the task but also enhances compatibility and compliance with current regulations and software requirements.
A streamlined setup entails several key steps that cater to specific functionalities. Familiarizing yourself with the correct protocols can significantly impact your user experience. Whether you’re looking to fine-tune system resources or optimize performance, having a clear setup guide is invaluable. From dealing with updates to ensuring access to necessary applications, each aspect contributes to the seamless operation of your machine.
Despite the more subdued environment of your device, complications can arise that require immediate attention. Addressing activation challenges or software issues can mean the difference between a productive session or a frustrating detour. By focusing on strategic solutions and leveraging well-defined procedures, you can maintain a smooth workflow and elevate your operational efficiency.
Keyverified product codes play an integral role in this procedure. These codes can be obtained through various sources, including official retailers and authorized partners. It’s vital to avoid using unverified or pirated keys, as this can lead to future complications, including system malfunctions and potential security risks.
The activation mechanism is generally straightforward: upon entering the key, the system verifies its validity with Microsoft’s servers. If successful, this process grants the user access to all the features of the operating system. For those wanting to leverage automated methods, seeking solutions for windows 10 silent activation might be appealing, as these approaches streamline the process significantly.
| Requirement | Description |
|---|---|
| Valid Product Key | Alegitimate code purchased from a verified source. |
| Internet Connection | Required for verification and activation processes. |
| Device Compatibility | Must meet hardware requirements specified by Microsoft. |
| Regional Settings | Key should match the device’s regional configuration. |
By understanding these activation requirements, users can ensure their devices are correctly configured, reducing potential errors and enhancing overall efficiency. Always prioritize securing a genuine keyverified code for the best results.
Once these specs are confirmed, perform a thorough check of your system to ensure all necessary drivers are up to date. Outdated drivers can lead to complications during the activation phase. Use device management tools to ascertain that each component, particularly the graphics and network drivers, is functioning optimally.
Next, if you’ve previously installed a key, check its validity. This is critical; using a keyverified license can save you time and hassle. You can confirm your key’s status through various third-party websites offering verification services.
Also, ensure that your device has a stable internet connection. During activation, connectivity issues may result in failure, which can lead to unnecessary frustration. A wired connection is often more reliable than Wi-Fi, so consider this for the activation process.
| Preparation Steps | Details |
|---|---|
| Check System Requirements | Minimum 16 GB storage and 2 GB RAM |
| Update Drivers | Ensure all drivers are current, especially graphics and network |
| Validate License Key | Use keyverification services to check license status |
| Ensure Internet Connectivity | Prefer wired connection for stability during activation |
By following these essentials, the activation process can proceed without significant interruptions, leading to a smoother experience overall. Prioritize these steps as they are crucial for success. Stay organized, and you’ll find yourself ready in no time.
1. Installation Preparation: Before starting, gather your license key. If you purchased a digital copy, it can typically be found in your Microsoft account or on the confirmation email. In addition, check if your device is updated to the latest firmware, as outdated versions may prevent proper function.
2. Connect to Wi-Fi: A stable internet connection is essential for any verification process. Access the settings menu, locate Wi-Fi options, and connect to a reliable network. Ensure signal strength is stable to avoid interruptions during activation.
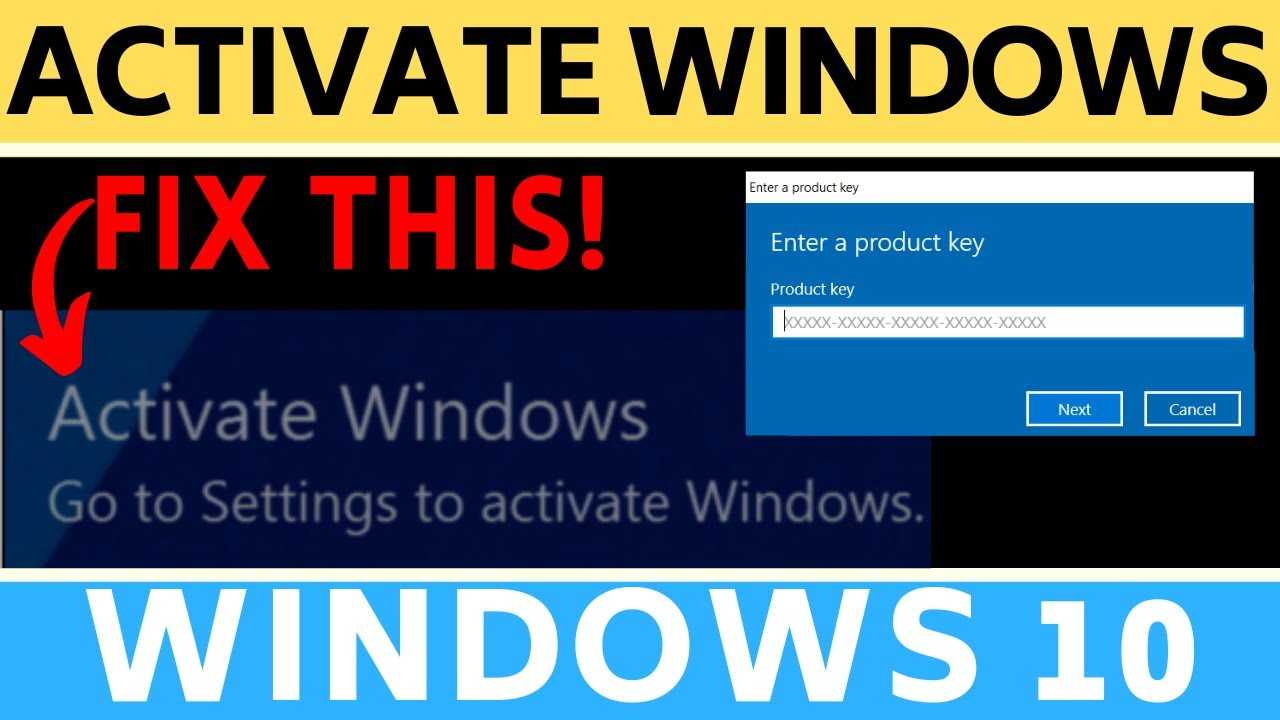
3. Accessing Settings: Navigate to the settings menu. This can usually be done by selecting the gear icon on the home screen or by swiping from the edge. Subsequently, select ‘Update & Security’ followed by ‘Activation’ to begin the activation process.
4. Entering the Product Key: Opt for the “Change product key” option within the activation settings. Input your 25-character license key precisely, noting that any errors can trigger activation failure. Confirm the entry to proceed.
5. Online Verification: The system will now connect to Microsoft servers to verify your key. This may take a few moments, depending on your internet speed. Watch for notifications indicating a successful verification or any issues that need addressing.
6. Dealing with Error Messages: If an error arises, refer to the official Microsoft support page for troubleshooting tips. Common issues may include network configurations or regional restrictions impacting activation. Adjust settings accordingly.
7. Final Steps: Once verified, the system should display a confirmation message indicating activation success. Should it not appear, revisit the steps or reach out to Microsoft support for further assistance.
Here is a summary of the key steps in tabular format:
| Step | Action |
|---|---|
| 1 | Prepare your license key |
| 2 | Connect to a stable Wi-Fi network |
| 3 | Access ‘Update & Security’ in settings |
| 4 | Enter the product key |
| 5 | Verify online |
This step-by-step approach simplifies what can be a frustrating process. Following these instructions will make enabling the operating system a more manageable task.
Check Network Connection: Ensure that the device is connected to a stable Internet. A weak or inconsistent connection can prevent successful verification. Try switching to a different Wi-Fi network or check the router settings if the issue persists.
Verify Product Key: Issues can arise when using an incorrect or previously used key. Confirm that the key entered reflects an unassigned or valid product. Use tools like Keyverified to cross-check the authenticity.
Windows Update: Keeping the device updated can resolve various bugs that hinder activation. Navigate to Settings, select Update & Security, and click on Check for updates to make sure the latest patches are installed.
Run the Activation Troubleshooter: Windows includes built-in troubleshooting tools that can automatically detect and fix activation-related issues. Access this feature by going to Settings, then Update & Security, and selecting Activation. Follow the prompts to initiate the process.
Table: Common Activation Issues and Solutions
| Issue | Solution |
|---|---|
| Invalid Product Key | Double-check the entered key; use Keyverified to confirm. |
| Activation Server Unreachable | Verify network connection; consider restarting the router. |
| System Updates Pending | Check for updates and install any available patches. |
By following these steps, most verification problems can be resolved swiftly. More detailed support is available through resources like the [Microsoft Support page](https://support.microsoft.com) for additional assistance in the USA.
When it comes to system setups, document your installation process, especially if you’ve customized installations. This can assist in replicating or troubleshooting your setup later.
| Storage Method | Pros | Cons |
|---|---|---|
| Password Manager | Encrypted, accessible across devices | Dependent on software security |
| Physical Copies | Always accessible, no tech required | Can be lost or damaged |
| Cloud Storage | Access from anywhere, easy sharing | Requires internet, risk of breaches |
Maintaining an organized approach is key for seamless usage, particularly with scenarios like using multi-user setups that may require frequent reactivation.
In case of loss of key, familiarize yourself with the recovery process through Microsoft’s support resources, ensuring you’re prepared for any unexpected challenges.