Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

The unexpected failure of storage devices can leave users in a lurch, particularly in scenarios where vital activation codes are encrypted within the system. A silent malfunction may result in unrecoverable data, but navigating your options can mitigate the impact of such mishaps. Knowing how to conduct a silent disk fix allows users to regain access to their important information, including the elusive activation data needed to restore their systems effectively.
Utilizing tools that facilitate the retrieval of the activation code offline is essential for those caught in this predicament. OEM keys stored in the firmware are often the last bastion for recovery efforts. Various utilities can extract this data even when conventional pathways to the operating system are compromised. Moreover, understanding the mechanics behind digital licenses plays a crucial role in preserving the integrity of your software environment amidst hardware failures.
This article explores advanced techniques for accessing your activation data after a storage device’s sudden decline, offering practical advice on how to proceed without an available backup. Whether you are a casual user or a tech-savvy individual, gaining insights into recovery tools and methods will empower you to handle such emergencies with confidence.
Another method involves utilizing the Command Prompt. By running a simple command, users can often extract the embedded code. Open Command Prompt and input wmic path softwarelicensingservice get OA3xOriginalProductKey. This command can yield the activation code directly from the system’s BIOS.
For those who seek solutions to retrieve their activation information offline, third-party applications may also assist. Tools like OEMKeys can be particularly useful, scanning hardware for stored information without needing internet access. However, ensure any software used is reputable to avoid security risks.
It’s advisable to create a backup of this critical information. Save the activation code to a physical document or a secure digital location to prevent future accessibility issues. This proactive measure can save valuable time during potential hardware replacements or upgrades.
When traditional methods fail, utilizing the Command Prompt can prove beneficial for obtaining your software activation credentials.
Here’s a straightforward guide to seek out your activation credentials through Command Prompt:
wmic path SoftwareLicensingService get OA3xOriginalProductKey
This approach allows those operating without internet access to perform key retrieval offline, ensuring you can proceed with reinstallation or troubleshooting.
For those with OEM systems, this method can effectively extract OEM keys that are embedded in the motherboard’s firmware, making it particularly useful when the original documentation is lost.
It’s essential to back up any credentials retrieved, especially when regularly managing software installations. This quick and straightforward command-line method can expedite the process of obtaining your activation credentials, keeping your system functioning smoothly.
For further assistance, consider exploring comprehensive key retrieval guides online that discuss various aspects of software licensing, including those tailored for specific manufacturers.
Utilize built-in recovery options available in your system settings. These tools can often help restore your environment to a previous state, ideally one where everything functioned correctly. Make sure to create restore points regularly, as this can be a quick recovery method in case of failures.
If you have previously configured a backup to an external storage or cloud service, retrieving your files becomes straightforward. Ensure that your backup software is up to date and includes the latest data versions to ensure a smoother recovery process.
For those with OEM keys, it’s vital to understand their specifications. They are often specific to the manufacturer and can be beneficial when reinstalling or activating the software. However, when attempting to recover a copy offline, ensure that you have the necessary documentation or support from the original vendor to assist you if complications arise.
Should you need assistance with choosing the right method or understanding what options might be best suited to your situation, how to choose the right Windows key can provide insightful guidance. By exploring trusted resources and comprehending options available, you can seamlessly navigate through potential obstacles.
| Solution | Description | Key Considerations |
|---|---|---|
| System Restore | Revert your system to a previous working state. | Requires creation of restore points. |
| File Backup | Recover files from external drives or cloud services. | Ensure regular backups are automated. |
| OEM Support | Use original manufacturer’s keys for reinstallation. | Proficiency in retrieval documentation is necessary. |
Log into your Microsoft account via the official website. Navigate to the “Devices” section where registered products are displayed. If your installation was digital, the associated product details should be visible here. Utilize this feature as a key retrieval guide, especially useful for users employing the offline recovery methods.
In cases where the digital license is tied to your account, you might not see the alphanumeric string packed into the traditional key format. Instead, look for annotations indicating active status for your installations. This serves as a silent disk fix, enabling reactivation without a physical code.
Moreover, maintaining an up-to-date registration is crucial. Regularly check your account settings to ensure all devices are accurately reflected. Should difficulties arise during the offline recovery process, reaching out to Microsoft support for additional guidance can streamline attempts to verify ownership and retrieve necessary activation credentials.
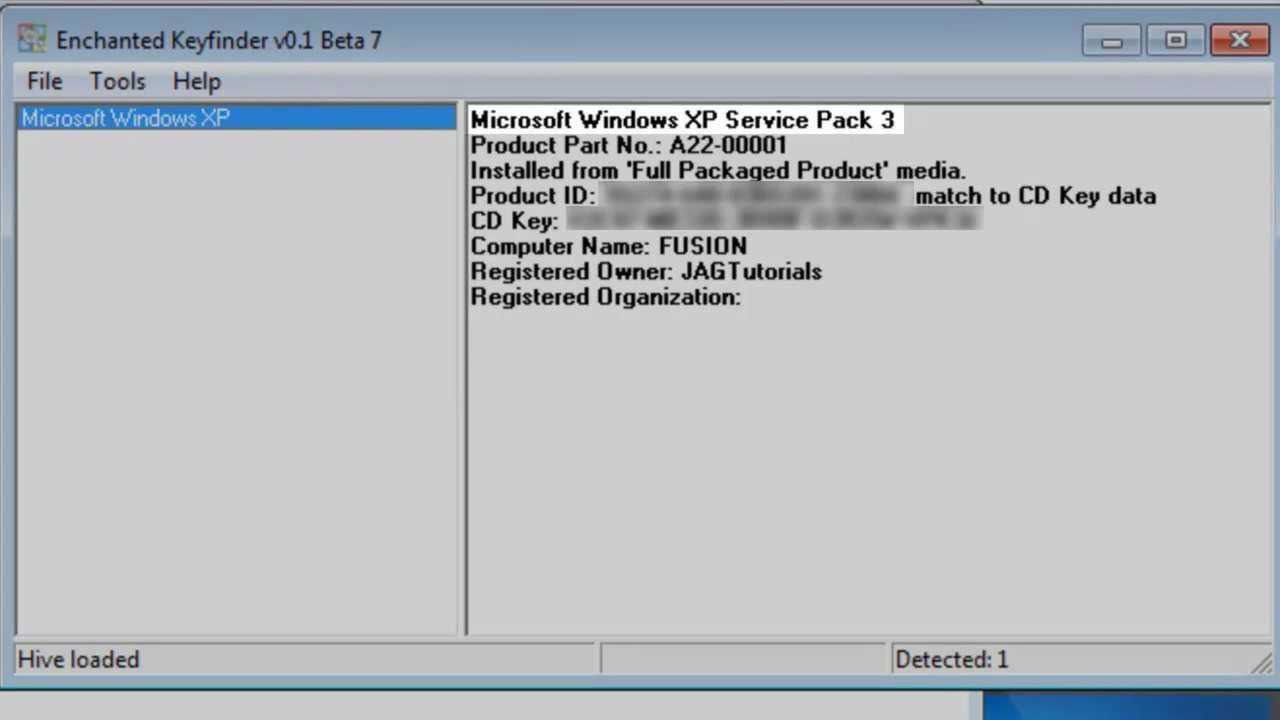
One notable trend is the rise of tools that enable offline extraction of activation licenses. These applications typically scan the local storage to locate identifiers stored in the system registry or other accessible files. This method is particularly useful when standard recovery options are unavailable due to system issues. To utilize such technology, download the tool from a reputable source and follow the built-in instructions to locate the activation details.
An example is the implementation of tools that can pinpoint and extract relevant data from the operating environment, offering users straightforward retrieval processes. In many cases, a simple click on the designated function prompts the application to pull necessary codes directly from the system’s architecture, providing a hassle-free experience in obtaining vital information.
However, one must proceed cautiously when selecting third-party applications. Always verify their credibility by researching user reviews and ratings. Tools that consistently receive positive feedback for user-friendliness and reliability are ideal candidates. This helps in avoiding malware or unreliable software that might compromise system integrity.
For users seeking to automate their recovery attempts, batch processing features in certain applications facilitate the extraction of keys from multiple installations, streamlining the process significantly. This capability is essential for tech-savvy users managing several machines, ensuring efficiency in cumbersome environments.
Once the activation codes are retrieved, ensure they are securely stored in an easily accessible manner, such as password managers or encrypted files. This practice minimizes the risk of future complications and provides a safety net during system restorations.
To resolve underlying issues related to data retrieval, consider implementing solutions such as a silent drive fix, which can potentially prevent future data loss. Regular backups and consistent monitoring of hardware health are essential to sustain long-term system stability.