Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

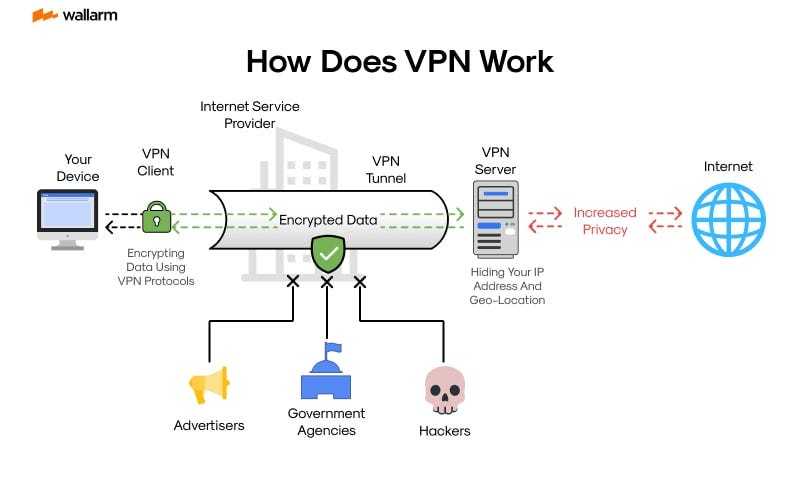
In the context of remote collaboration, 2025 presents specific challenges regarding privacy and security during virtual discussions. The shift towards high-definition communication platforms necessitates a reliable method of safeguarding sensitive conversations. With increasing reliance on online meetings, adopting practices for vpn silent work meetings has become paramount in ensuring confidentiality.
The integration of protocols like WireGuard, which boasts a significant reduction in latency, greatly enhances user experience. As companies adapt, understanding the 2025 basics of secure communication tools is crucial. Fast and efficient solutions are no longer options, but rather necessities for organizations prioritizing data protection and employee privacy during discussions.
Among numerous options available, tools that utilize advanced encryption standards are vital. Services such as ExpressVPN have paved the way through exceptional performance and ease of use. Ultimately, selecting the right resources ensures that teams can engage in discussions without fear of interception or data leaks, enabling a more secure professional environment.
Here are some basics to guide your decision:
Recent trends show an increase in interest around VPN silent work meetings. This means there’s a growing focus on maintaining privacy without intrusive logging and tracking. Solutions that meet these needs often implement no-log policies, ensuring that user activity remains confidential.
As you explore options, consider a few notable providers:
Testing these services in your specific region is advisable to narrow down which one meets your performance standards. For those working in areas with stringent internet regulations, ensure that the chosen provider supports connectivity in these environments.
In summary, the selection process in 2025 demands careful consideration of encryption standards, latency requirements, and privacy policies. Balancing these factors will lead to a more secure and productive virtual collaboration experience.
Next, review your connection settings. Set default options to prevent DNS leaks, ensuring that all web traffic is routed through the encrypted tunnel. Modify your DNS settings to include secure resolvers, such as Cloudflare or Google Public DNS, which can enhance both security and performance.
Limit connectivity options by activating a kill switch feature. This will automatically disconnect your internet if the VPN connection drops, safeguarding your data from unintended exposure. For added safety during silent work discussions, utilize split tunneling. This allows you to decide which applications should connect through the VPN, providing flexibility for tasks that don’t require a secure connection.
Regularly change VPN passwords and monitor access logs to identify unauthorized attempts. If your provider offers advanced features like multi-factor authentication, enable it to further bolster account security. As threats evolve, staying informed through trusted sources will assist in maintaining a secure and adaptive strategy.
Many users may overlook the importance of seamless integration. A VPN plays a pivotal role in safeguarding data transmitted over VoIP services by encrypting connections and masking IP addresses, preventing potential breaches during silent work discussions. Ensuring that communication tools are configured to function effectively alongside a VPN ensures uninterrupted workflow. Businesses are now increasingly adopting solutions like ExpressVPN, known for its user-friendly setup and robust performance in corporate environments.
One key trend is the growing functionality of chat applications, where encryption is becoming an industry standard. Organizations are advised to adopt communication tools that offer end-to-end encryption while ensuring they are compatible with VPN technology. This synergy allows for smooth, protected interactions. As virtual meetings will continue to shape workplace dynamics, understanding the intersection of VPNs and communication platforms is essential for secure exchanges. Regular updates and patches for both VPN clients and communication applications further bolster security, maintaining a reliable framework for collaboration.
For an in-depth understanding of digital security protocols and their implementation in communication tools, resources from trusted sources, such as the Cybersecurity & Infrastructure Security Agency (CISA), are invaluable. They offer comprehensive guidelines and insights relevant to enhancing virtual protocols in the workplace.

Adopt a vpn silent work meetings approach to mitigate risks associated with unsecured networks. Ensure that your connection is always encrypted, especially when accessing public Wi-Fi. Make it a habit to check for security updates regularly; the latest updates often fix vulnerabilities that could jeopardize your privacy.
Establish a secured environment by disabling unnecessary devices and applications that may inadvertently leak information. Always utilize separate devices for confidential interactions–this minimizes the risk of accidental exposure through other logged-in accounts or applications.
In 2025, consider implementing multi-factor authentication (MFA) as a standard practice. This adds an additional layer of security and makes unauthorized access significantly more difficult. Always inform participants about best practices for safeguarding their devices and connections during discussions.
Lastly, familiarize yourself with the basics of secure communication technologies. Understanding the limitations and strengths of various tools can help you choose the right platform for your needs while maintaining the confidentiality of sensitive discussions.
Video calls require a stable connection, and specific bandwidth recommendations indicate that applications like Skype need between 10-20 Mbps for HD quality in 2025. Understanding typical challenges when connecting can enhance your experience significantly.
Common problems include:
For enhanced performance during digital interactions, consider these tips:
If you encounter activation problems with software keys, ensure you source them from trusted platforms. For instance, for utmost security and effective purchasing, tips on safe key purchase are invaluable resources.
Ultimately, addressing these issues will pave the way for seamless, silent dialogues in your virtual workspace.