Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10
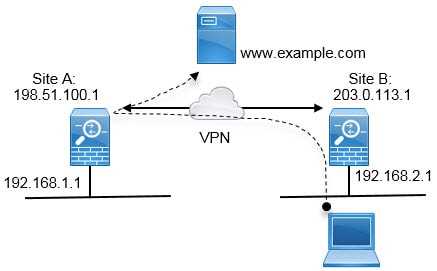

The evolution of communication technology has made audio-only conferences increasingly popular, particularly in remote work settings. As the demand for seamless and secure communication rises, understanding the 2025 basics of maintaining privacy during these sessions becomes vital. Using advanced protocols can significantly minimize risks associated with data breaches and unauthorized access.
A key component of this secure setup involves selecting the appropriate technology that ensures both speed and encryption. Key protocols emerging in 2025, such as WireGuard, are demonstrating substantial improvements in latency and overall performance. These advancements enable uninterrupted audio sessions while safeguarding sensitive information from potential cyber threats.
As organizations strive to implement best practices for secure audio engagements, tools like CyberGhost offer comprehensive benefits including user-friendly interfaces and robust security features. Evaluating various options will enhance privacy and provide a stable environment for productive communication. Prioritizing a secure digital environment is no longer just an option but a necessity as the virtual landscape evolves.
A secure setup is foundational. OpenVPN remains a widely accepted option due to its robust encryption standards and flexibility. It supports various ciphers like AES-256, which ensures data security without compromising speed. However, it may introduce a slight latency increase, which some users might notice in voice interactions.
WireGuard is gaining traction, known for its simplicity and minimal code footprint. This protocol establishes connections swiftly, cutting latency by as much as 40%, which is beneficial for uninterrupted voice calls. Its ease of configuration further attracts users seeking straightforward setup solutions.
When considering the impact of a VPN on voice communication, look into the performance metrics of various protocols. According to recent studies, adopting protocols that maintain low latency is advisable, with speeds around 150-250 Mbps being adequate for clear communication. Furthermore, the choice of server location plays a role; connecting to nearby servers typically reduces lag in audio transmission.
As users prepare for virtual interactions, understanding the basics of each protocol can help in making informed decisions. Examining user reviews on protocol performance in voice clarity can also provide insights and guide users toward the best fit for their needs.
For those prioritizing clarity and security in their virtual conversations, careful analysis of protocol characteristics and real-world testing will yield the best outcomes in 2025 and beyond.
Bandwidth Allocation: Allocate sufficient bandwidth specifically for voice calls. Aim for at least 10-20 Mbps for smooth high-definition audio. This helps in reducing interruptions during conversations.
Protocol Selection: Employ protocols like WireGuard, which is known for significantly reducing latency, boosting call quality. Comparing it to traditional protocols indicates up to 40% latency reduction, enhancing real-time communication.
Encryption Level: Opt for AES-256 encryption to secure your connection. This ensures a high level of protection while maintaining adequate speed for audio transfers.
Server Location: Choose servers geographically closer to your location. A closer server leads to lower latency, enhancing the clarity and responsiveness of voice calls.
Connection Stability: Enable options that maintain a stable connection. Features like automatic reconnection can help prevent dropouts during important conversations.
Quality of Service (QoS): If available, enable QoS settings on your router. This prioritizes audio traffic, ensuring that call data is transmitted smoothly over other forms of data, which is especially beneficial in shared networks.
While adjusting these settings, consider a secure setup that also embraces privacy. Services like CyberGhost provide user-friendly interfaces to manage these configurations easily, allowing you to focus on communication without technical distractions.
Testing your configuration with various tools can provide insights into where improvements can be made. Regular adjustments based on performance feedback will lead to ongoing enhancements in your call quality.
Begin your assessment by measuring baseline performance without a VPN. Tools like Ookla or Speedtest.net can help determine your connection speed and stability. Aim for at least 20 Mbps to maintain adequate performance during voice calls.
Once a baseline is established, employ a reliable VPN service such as CyberGhost. Various tests can provide insight into VPN effectiveness on audio quality. Notably, observe the following key performance indicators:
Conduct tests across different times of day to evaluate potential variations. For example, testing during peak usage hours can reveal how well your chosen virtual private network manages congestion. Additionally, a multi-server approach may help in identifying the best options available for voice services.
After applying the vpn in various configurations, analyze the effects on sound clarity. Record sessions with and without the VPN, noting the differences in audio quality. A comparison of sessions will help ascertain the VPN’s impact on the call experience.
In summary, a thorough evaluation process, relying on systematic testing and analysis, allows you to gauge the effectiveness of your selected VPN during virtual meetings. A secure setup not only protects your data but can also enhance the audio experience, allowing for clearer communication and fewer interruptions.
Below are some common problems and strategies to improve your experience:
Maintaining a consistent connection may require testing the above solutions diligently. For those experiencing ongoing challenges, consulting forums or support from the VPN provider can yield further assistance.
For additional insights on network issues, check the official Federal Communications Commission (FCC) resource. This site provides authoritative information on internet connectivity and ongoing issues affecting communications in the USA.
1. Choose Strong Encryption Protocols: Prioritize VPN providers that utilize robust encryption standards, such as AES-256. This ensures that data transmitted during virtual meetings remains confidential and shielded from potential cyber threats, such as eavesdropping or data breaches.
2. Regularly Update VPN Software: Keeping your VPN software up-to-date is crucial. CyberGhost and other reputable services frequently release updates that patch vulnerabilities and improve security features. Ensuring that your application is current diminishes the risk of exploitation by malicious actors.
3. Use Kill Switch Feature: A kill switch is a safety feature that automatically disconnects your internet connection if the VPN connection drops unexpectedly. This prevents any unprotected data from being transmitted unknowingly, thereby maintaining confidentiality during critical discussions.
4. Verify Server Locations: Opt for a VPN that provides servers located in jurisdictions with strong privacy laws. This is particularly relevant for professionals who handle sensitive information, as it reduces the risk of governmental authorities accessing your data.
5. Evaluate Connection Speeds: In professional settings, reliable connectivity is essential for smooth communication. Test your VPN’s speed regularly to ensure that latency does not interfere with voice clarity or lead to dropped calls.
6. Implement Multi-Factor Authentication: Enhance security further by enabling multi-factor authentication (MFA) where available. This adds an extra layer of protection by requiring additional verification steps when accessing the VPN.
7. Educate Users: It’s crucial to ensure all team members are aware of best practices concerning VPN usage. Conducting regular training on potential risks and safe usage can greatly reduce human error, which is often a weak link in digital security.
Incorporating these strategies can significantly enhance the security of your online discussions within a VPN environment. For further resources on network security and software management, consider exploring reliable ways to activate Windows as they often include security-focused insights and maintenance tips.