Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10
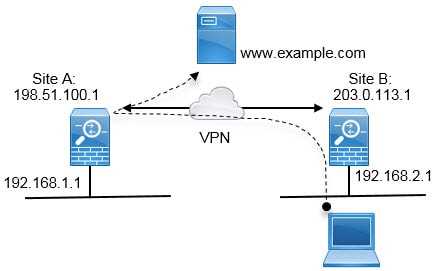

As we move toward 2025, the demand for safe and unobtrusive voice meetings is rising. Many professionals engage in conference discussions where audio clarity is crucial yet privacy cannot be compromised. The integration of innovative tools and practices can help secure these calls, ensuring that sensitive information remains confidential while participants stay connected seamlessly.
Understanding the fundamentals of maintaining security during these discussions is paramount. Techniques such as employing advanced protocols like WireGuard can significantly reduce latency and enhance call quality. Additionally, utilizing services that undergo rigorous testing for reliability establishes a solid foundation for uninterrupted communication. Users should prioritize features that focus on data protection and speed, making informed choices for their online presence.
Amid the saturated market of security services, options like CyberGhost are gaining traction. These platforms not only focus on ease of use but also provide robust frameworks that bolster user anonymity. As professionals assess their options for the upcoming year, ensuring compatibility with various devices and platforms remains a priority to foster greater flexibility in communication.
When assessing features, focus on services offering AES-256 encryption as a standard to ensure robust protection against eavesdropping. Look for those with a no-logs policy as this displays a commitment to safeguarding your data and privacy. Latency rates and server distribution are instrumental as well; select options that boast optimized speeds and extensive server networks in your primary region to ensure stability.
Comparing different choices is vital. Some services like Cyberghost provide user-friendly interfaces while maintaining solid performance. Others may excel based on price and flexible plans, making them suitable for startups or budget-conscious users. Exploring independent reviews can shed light on real-world experiences and features that might be beneficial in your specific scenario.
For those considering integrating less common routes into their tools, remember that newer options often bring enhanced protocols and lower pricing to remain competitive. This can be explored further through performance tests available from independent sources like Ookla, showcasing speeds and reliability across various service providers.
As the atmosphere surrounding online discussions continues to evolve, a well-chosen partner will not only secure communications but also enhance productive collaboration. Check comprehensive resources such as Consumer Reports for further information on selecting a trustworthy provider tailored to your needs.
Start with a connection that has at least 10-20 Mbps to support high-definition audio streams. This speed is crucial for platforms known for their bandwidth demands, ensuring clarity and minimal interruptions. Utilize settings that prioritize this bandwidth by limiting background applications that consume significant data.
Choosing the right protocol can also enhance audio performance. A modern and efficient option like WireGuard has been shown to reduce latency by up to 40% (source: Wikipedia), providing a more responsive experience during calls. Ensure your configuration allows for rapid reconnections as network conditions fluctuate.
Moreover, managing Quality of Service (QoS) settings in your router can allocate bandwidth more effectively for voice communication. By prioritizing audio packets, you reduce the risk of packet loss, which is vital for maintaining audio quality throughout the conversation.
Investing in services like CyberGhost can also bring tangible benefits. The combination of robust encryption and efficient data routing enhances both privacy and call stability. For a secure setup, avoid using public Wi-Fi for important calls unless absolutely necessary, and consider using a wired connection for improved reliability.
Lastly, reviewing your hardware is vital; ensure microphones and speakers are optimized for use with various platforms. Incorporate these adjustments for a smoother, clear communication experience–these techniques can make a significant difference in audio performance during your virtual engagements. For purchasing encryption keys, learn how to pick a store for key purchase.
In the quest to ensure confidentiality during communications, end-to-end encryption becomes critical. This setup guarantees that only participants in a conversation can access the audio, effectively shielding conversations from external access.
To establish a secure framework, consider the following:
For optimal confidentiality, using trusted software is essential. Some notable examples include communications platforms that integrate protocols ensuring robust protection.
To enhance your setup, incorporate CyberGhost as it employs reliable encryption methods, providing an additional layer of security during conference sessions. This service effectively supports anonymous communication without sacrificing quality.
In summary, implementing a secure configuration for audio discussions involves multifaceted strategies. By utilizing advanced protocols and trusted tools, participants can maintain privacy and integrity in their conversations.
Latency, ideally less than 50 ms, significantly impacts the clarity of voice communication. Regularly monitoring can reveal fluctuations that might indicate issues with your service. A ping test using services like Speedtest can help gauge if your current connection meets requirements for uninterrupted discussions.
Jitter should also be kept under 30 ms. High jitter can cause audio to drop or distort, making it challenging to engage meaningfully in your vpn silent audio conference. Monitoring these parameters in real-time will assist in identifying potential problems early on.
For a more in-depth analysis, consider using tools that allow you to check the stability during the call. Applications that log performance metrics can provide insights that are essential for troubleshooting during discussions. This proactive approach ensures that you can adapt quickly by switching to alternative setups if necessary.
In 2025, staying informed about network troubleshooting basics will help maintain a seamless experience. Learn about common pitfalls such as bandwidth hogs within your network. Encourage team members to limit uploads and downloads during critical calls, thereby preserving bandwidth for clear audio transmission.
Employing these practices consistently will lead to improved sound quality and fewer interruptions, ultimately enhancing the overall experience of your conversations.
As remote work becomes more common and virtual meetings dominate business interactions, it’s crucial to safeguard private conversations during these sessions. Understanding emerging trends and employing effective measures can significantly enhance protection against potential threats.
Start by opting for reliable connection methods that emphasize data encryption. Leverage protocols like WireGuard, which is gaining attention for its speed and security features. In 2025, the basics of internet communication will demand such advancements, ensuring that all transmitted data remains confidential and secure.
Employ role-based access controls during group discussions. Restricting entry to relevant participants minimizes exposure to sensitive information. This method is particularly effective during critical decision-making calls or discussions about proprietary content.
Ensuring a stable and private network connection is fundamental. Opt for dedicated internet services or utilize services like CyberGhost, known for their focus on user privacy, reducing the risk of unauthorized data interception.
Always conduct audio tests before crucial meetings. A clear line helps ensure participants can communicate effectively while removing the temptation for any unauthorized recording. Moreover, consider utilizing modern applications that provide additional layers of encryption to your conversations, ensuring that even if data is intercepted, it remains incomprehensible.
To bolster preparedness, cultivate a culture of security awareness. Regularly educate team members about identifying potential threats, such as phishing attempts or social engineering tactics. Understanding these risks prepares them to act promptly if they encounter suspicious activity.
Remember that compliance with industry regulations, such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare communications, is essential when discussing sensitive topics online. Following established standards ensures that organizations protect their data and avoid penalties.
| Practice | Description |
|---|---|
| Data Encryption | Use protocols like WireGuard for encrypted connections. |
| Role-Based Access | Limit access to participants who need it. |
| Private Network | Utilize secure internet services to minimize interception risks. |
| Regular Training | Conduct frequent sessions on identifying security threats. |
| Regulatory Compliance | Adhere to laws relevant to your industry concerning data protection. |