Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

In recent times, users have noticed significant challenges in software activation processes due to unexpected memory strain on their systems. The impact is evident when attempting to validate purchased licenses. As various digital ecosystems evolve, the need for reliable and quiet tools to streamline this procedure has never been more critical. Insights into this situation indicate that identifying new strategies can enhance the user experience while mitigating frustrations tied to system performance.
The marketplace offers a range of solutions that cater to the identification and recovery of keys under pressure. Leveraging the right tools can provide clarity in situations where the integrity of product codes comes into question. Innovative methods have emerged to address the disarray that may arise when heavy memory usage disrupts typical activation flows. Many users have reported positive outcomes by utilizing lesser-known platforms, highlighting the importance of having diverse options to smooth the activation process.
As you delve into the various techniques to recover your software key, utilizing resources such as oemkeys can considerably simplify your endeavors. By embracing technology tailored for specific challenges, users can restore functionality efficiently. Stay informed about the most effective strategies to safeguard your digital assets and enjoy uninterrupted access.
First, check the Task Manager to monitor real-time memory usage. Applications consuming excessive RAM can create bottlenecks. Look for processes that stand out, particularly those linked to productivity suites. In many cases, dormant applications or background services might need to be terminated to free up valuable resources.
Another method involves observing system performance during heavy tasks. Users may note slowdowns not just in activation but across all applications, indicating a more systemic issue. Regularly scheduled maintenance, such as cleaning unnecessary files or optimizing system settings, can help alleviate pressure on memory.
Using tools that manage quiet processes can also aid in identifying potential conflicts. These utilities prevent unwanted applications from consuming memory while running in the background. Users should explore various quiet tools to customize their system’s settings, allowing for optimized performance without unnecessary interruptions.
OEM keys acquired through reputable channels provide additional integrity during activation. Ensuring that activation methods align with system specifications is crucial. In situations where overload is evident, a detailed inspection of both hardware and software configurations may be necessary to address underlying issues.
Firstly, make sure to obtain and securely store your activation code. This code can typically be found in the confirmation email you received when you made your purchase or within your Microsoft account, depending on how you acquired the software. If you purchased from a third-party supplier, like comparison of sites with Windows licenses, verify the details of your purchase to locate the code.
Follow these straightforward steps to reinstall the program:
In cases where you encounter difficulties, it may be beneficial to review the manufacturer’s help documentation or support forums specifically designed for troubleshooting installation issues related to your version. Remember that maintaining your activation code safely is pivotal for future usage, particularly when facing technical challenges.

Implementing these practices can help mitigate potential problems with your installation key and ensure that software remains activated without interruptions. Regular maintenance of RAM is thus a key component in enhancing system stability and performance.
For more serious issues related to memory management, looking into dedicated tools may provide additional benefits, offering better visibility and control over how resources are allocated.
Begin by launching Command Prompt as an administrator. This can be achieved by searching for it in the Start menu, then right-clicking and selecting ‘Run as administrator’. Once you have the elevated command prompt open, you can employ various commands to help remedy problems.
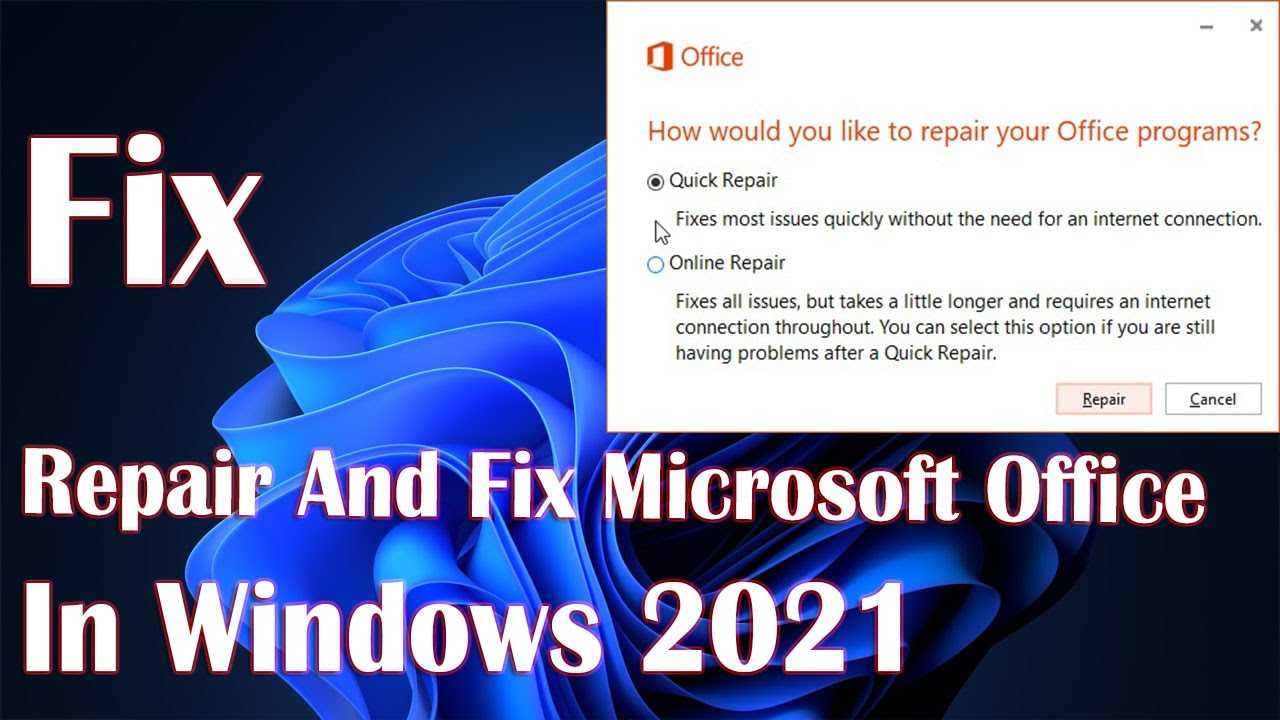
A prevalent command to try is OfficeC2RClient.exe repair, which addresses installation concerns associated with your Microsoft suite. This command can help restore normal operation and eliminate errors stemming from memory overload situations.
In addition to the standard repair command, consider using DISM /Online /Cleanup-Image /RestoreHealth. This process checks for corruption in Windows components that can affect installed applications, including your software package. Running this can sometimes resolve deeper issues unlinked to the memory strain directly.
Quiet tools in Command Prompt can yield significant results without the need for complicated software or lengthy troubleshoot procedures. After executing the repair commands, reboot your device to observe if performance stabilizes. Monitoring system performance and application responsiveness thereafter is crucial to determining the success of the intervention.
If you continue to experience difficulties, reviewing the error codes and messages produced by the commands may provide insight into specific problems. These could signify the need for further investigation or even reinstalling the entire software suite. By leveraging these efficient tools, many find their issues resolved, returning to seamless productivity.
Remember that regular maintenance of your machine’s memory and application management can mitigate similar issues in the future. Establishing preventative practices will help maintain a stable environment for all your software applications.
Before contacting, gather necessary documentation, including the initial email confirmation and purchase receipt. These details simplify the verification process and expedite assistance. Microsoft Support can assist via chat, phone, or community forums, each option providing different levels of immediacy and personalization.
Utilizing specific reference numbers associated with your purchase aids the support team in locating relevant information swiftly. This method is particularly effective if you’ve purchased from recognized suppliers, such as those highlighted for distributing discounted licenses. Whether for a factory-installed software version or a standalone product, detailing your situation allows representatives to analyze and recommend suitable recovery methods tailored to your case.
For users seeking alternatives post-recovery, exploring options like oemkeys can offer additional flexibility and potential savings on future licenses. Keep in mind that Microsoft usually retains records of product keys and can retrieve them under most circumstances, provided the appropriate evidence is presented.