Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10


In the realm of technology, disruptions in high-speed internet, particularly 5G connectivity, can inadvertently lead to a series of complications for users reliant on digital services. These interruptions often result in authentication hurdles that may compromise user access to essential software. With many individuals upgrading their systems, the loss of activation information becomes a more prevalent concern. This discussion focuses on how to address such challenges efficiently while ensuring continuous access to required applications.
This recovery guide offers practical strategies to retrieve activation credentials in situations where connectivity issues, such as 5G drops, have hindered access. It emphasizes crucial methods that can be employed to safeguard and regain vital digital access points, ensuring a seamless transition back to productivity. The following sections illustrate user-friendly steps tailored to tackle the unique scenarios that arise when experiencing connectivity setbacks.
By breaking down the processes involved in regaining access to activation data, users can better understand how to mitigate potential losses. This guide intends to transform what could be a frustrating experience into an opportunity to enhance one’s technical resilience, ultimately supporting a more robust approach to managing digital resources amidst occasional connectivity flares.
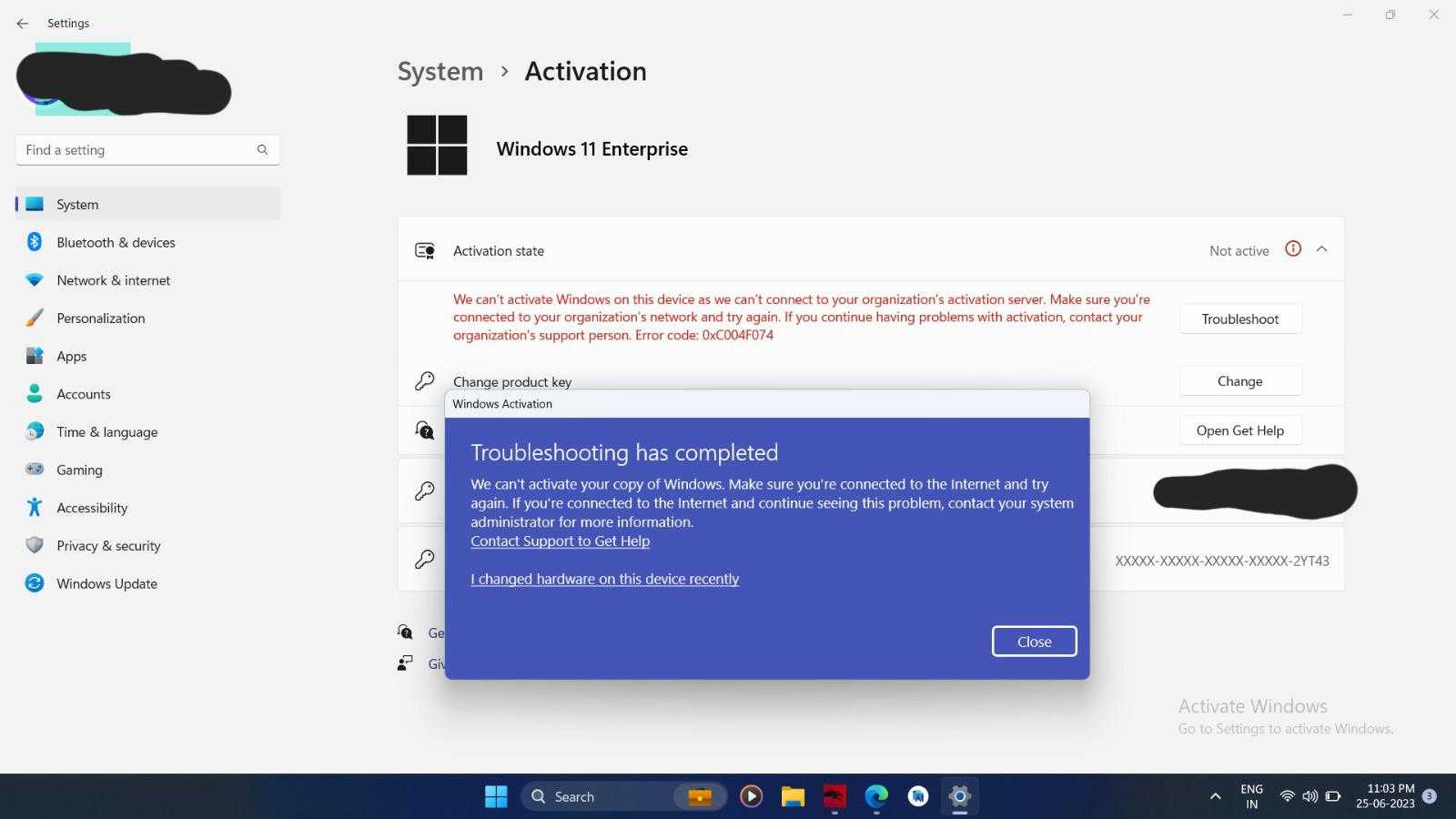
If you experience these symptoms, following a recovery guide specific to issues arising from network disruptions might help restore your activation status. Consider these actionable steps:
The table below outlines common activation error codes encountered during these instances:
| Error Code | Description | Suggested Action |
|---|---|---|
| 0xC004C003 | The activation server reported that the product key is blocked. | Contact support for resolution. |
| 0xC004F074 | The activation server cannot be reached. | Verify the network connection. |
| 0xC004F061 | The product key is invalid. | Double-check the key entry or obtain a new one. |
By recognizing these signs and following a structured recovery approach, issues related to your activation status can often be resolved effectively. Stay proactive with your activation measures to ensure seamless functionality.
If you encounter challenges getting your activation code back, the Command Prompt provides a straight path for retrieval. Here’s a step-by-step guide tailored to extract your license identifier via this built-in utility. Ensure to run Command Prompt with elevated privileges for the best results.
Follow these steps to successfully obtain your activation code:
wmic path softwarelicensingservice get OA3xOriginalProductKeyThis method allows for quick access to your activation information, proving especially effective if you face turmoil with your 5G connectivity impacting recovery methods. Keeping records of your key through efficient means can be a lifesaver in instances where you’re engaged in critical tasks.
| Step | Command |
|---|---|
| 1 | Open Command Prompt as Administrator |
| 2 | wmic path softwarelicensingservice get OA3xOriginalProductKey |
| 3 | Record the displayed product identifier |
This straightforward technique simplifies the process of obtaining your activation code. Predictably, issues such as a 5G drop may hinder other recovery tactics, making this approach a practical alternative worth considering, ensuring you always have access to keyverified information at your fingertips.
To retrieve your activation credentials amidst 5G drop fix scenarios, the Windows registry serves as a valuable resource. By following these steps, you can navigate to the relevant sections and extract the necessary information discreetly.
1. Press Windows + R to open the Run dialog box. Type regedit and hit Enter to access the registry editor.
2. In the left sidebar, navigate to the following path:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersion
3. Look for a subkey labeled DigitalProductId. This key usually contains the encoded product details essential for the verification process.
4. To decode the alphanumeric string found in the DigitalProductId, you may require third-party tools specifically designed for this purpose. They can deobfuscate the information effectively.
Here’s a concise table to summarize the process:
| Step | Action |
|---|---|
| 1 | Open Run dialog and type regedit |
| 2 | Navigate to HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersion |
| 3 | Locate DigitalProductId |
| 4 | Use third-party tools for decoding |
Utilizing the registry for product details is an efficient method when facing connectivity challenges. This approach not only provides a workaround but also aids in ensuring your system remains fully operational. For more guidance, explore reliable resources or tools focused on activation processes.
When faced with the unexpected disappearance of a crucial software identifier during technological disruptions, employing specialized applications can be a practical solution. This recovery guide highlights several reputable tools that streamline the process of extracting licenses and other critical information.
One standout option is Keyverified, known for its user-friendly interface and effective scanning capabilities. This software scans the system deeply, uncovering hidden codes that may not be easily accessible through traditional methods. It’s particularly beneficial if your device experiences connectivity interruptions, as it does not rely solely on cloud-based retrieval.
| Software Name | Features | Platform |
|---|---|---|
| Keyverified | Quick Scan, License Backup | Windows, Mac |
| Magical Jelly Bean | Bulk Retrieval, Export Options | Windows |
| Belarc Advisor | System Audit, License Management | Windows |
For those contemplating options, consider the intended functionality of the software. Is it aimed solely at recovery, or does it offer additional system management tools? Tools like Belarc Advisor not only identify lost codes but also provide an overall snapshot of installed software–a handy feature for comprehensive system maintenance.
Next, evaluate user reviews and ratings, as community feedback often illuminates practical experiences that official descriptions may overlook. Many users find reassurance in tools that offer backup capabilities; these ensure that copies of identified identifiers are securely stored for future reference.
With an array of software solutions available, selecting the right application for extracting your software identifiers can significantly simplify the process during tech upheavals. By leveraging the right tools, you can avoid unnecessary frustrations and swiftly recover essential licensing information.
To fortify your setup against potential license mishaps stemming from connectivity hiccups, consider implementing a few proactive measures. Here’s a focused recovery guide to ensure your valuable access codes remain safe.
1. Utilize Offline Activation: Whenever possible, opt for offline activation methods. This allows you to secure your essential access without relying on an active data connection, thus shielding you from any disruptions caused by fluctuations in your service.
2. Regular Backups: Incorporate periodic backups of your activation details. Store these in a secure location–both on an external drive and in a cloud storage solution. This dual approach guarantees that you’ll always have a recovery option available, regardless of network status.
3. Check Your ISP Performance: Monitoring the reliability of your internet service provider can help preempt issues. Tools like Speedtest can give you insights into network speeds and stability, indicating when it might be time to switch providers or upgrade your current plan.
4. Utilize Keyverified Tools: There are various tools available that can securely store and retrieve your activation codes. Emphasizing keyverified solutions ensures that your data remains encrypted and easily accessible when you need to retrieve it, providing an additional layer of protection against loss.
5. Stay Updated: System updates often include security improvements and performance enhancements. By keeping your operating environment updated, you minimize vulnerabilities that could lead to disruption during critical times.
6. Avoid Large Downloads/Uploads: Ration your bandwidth usage when crucial tasks are at hand. Engaging in heavy downloads or streaming while performing important software activations could lead to interruptions, rendering the process invalid.
| Tip | Action |
|---|---|
| Offline Activation | Use methods that don’t require a live internet connection. |
| Regular Backups | Store access codes both locally and in the cloud. |
| ISP Performance | Monitor your internet connection for consistency. |
| Keyverified Tools | Utilize encrypted solutions for safe storage. |
| System Updates | Keep your system current with the latest patches. |
Implementing these strategies can significantly fortify your defenses against unexpected loss of software access due to unstable connections. Empower yourself with knowledge and tools to maintain uninterrupted performance and peace of mind.