Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10
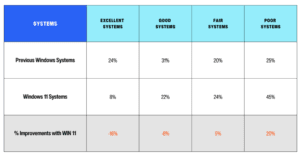
In the realm of operating systems designed for professional environments, there are distinct variations that cater to varying organizational needs. The business-focused editions offer a range of enterprise tools that enhance productivity and streamline workflows. When assessing these versions, organizations must consider the specific features that align with their operational requirements, particularly when it comes to scalability and security.
One significant aspect that sets these editions apart is the suite of security enhancements they provide. While both versions include robust protection mechanisms, the advanced security protocols found in the more comprehensive option are tailored to safeguard sensitive data and manage threats effectively. This includes advanced encryption techniques and sophisticated identity protection measures that cater to larger teams working with critical information.
Additionally, the approach to IT management varies between these two offerings. The more extensive version includes features like centralized deployment and management tools, empowering IT administrators to maintain control over devices seamlessly. This can lead to reduced operational burdens and improved compliance with organizational policies. An understanding of these pricing differences is also crucial, as the financial implications may influence a company’s decision on which edition best suits their infrastructure.
When choosing between various editions of operating systems, it’s crucial to examine the licensing structures that accompany each version. This not only affects cost but also business processes and the tools available for IT management.
Organizations must consider how licensing decisions impact overall productivity. For instance, corporate clients may benefit from access to advanced features and enterprise tools tailored to enhance workflow efficiency:
Pricing can vary significantly based on the chosen licensing model. It is essential to evaluate:
Understanding the differences in licensing models is vital for businesses aiming to maximize productivity while ensuring proper IT management. By evaluating tools tailored to organizational needs and factoring in pricing, companies can make informed decisions that enhance overall operational efficiency.
In the competitive environment of IT management, selecting the right operating system can significantly influence business productivity. Among the various attributes available, security enhancements like BitLocker and Windows Defender stand out for their capabilities in safeguarding sensitive data and protecting systems from threats.
BitLocker is a built-in encryption tool designed to protect data by encrypting the entire drive. This feature is crucial for organizations handling sensitive information, as it helps prevent unauthorized access in the event of theft or loss of a device. Key aspects of BitLocker include:
Due to its integration with various IT management tools, BitLocker not only strengthens security but also aligns with the organization’s overall compliance strategy.
Complementing BitLocker’s data protection, Windows Defender offers extensive real-time protection against malware and other security threats. Its features contribute significantly to maintaining system integrity:
This tool not only secures endpoints but also enhances overall productivity by minimizing downtime caused by security breaches.
Organizations must assess the pricing associated with these security tools in light of their features. While both tools are included in many versions of the operating system, enterprises should evaluate whether the additional benefits justify any potential costs associated with deployment across multiple systems.
In summary, the robust capabilities of BitLocker and Windows Defender make them vital components in bolstering security frameworks. By incorporating these tools, businesses can significantly enhance their data protection strategies while fostering a culture of security awareness among users. The balance between cost and security features ultimately supports a safer and more productive business environment.
In the realm of IT management, advanced tools play a crucial role in enhancing operational efficiency and security. These utilities are designed to cater to the needs of professionals who require comprehensive control over devices and networks.
Key attributes of these management solutions include:
When considering pricing for these enterprise tools, organizations must evaluate the total cost of ownership, including licensing, support, and any associated infrastructure requirements. These considerations are crucial in determining the return on investment and overall value for the business.
Additionally, specialized features tailored for IT management facilitate automation of routine tasks, freeing up resources for more strategic initiatives. Automation minimizes human error and enhances productivity across teams.
In conclusion, embracing advanced management tools not only streamlines IT operations but also provides IT professionals with the capabilities to safeguard their organizations while maintaining efficient workflows. Investing in these tools is an important step towards achieving a more secure and well-managed IT environment.
Organizations often seek to enhance their business productivity through optimized application deployment strategies. Selecting the right operating system version can significantly influence IT management and support capabilities. Both editions offer distinct pathways for deploying applications and managing licenses effectively.
The following are common deployment options available in various versions:
Each edition also boasts enhanced security enhancements that assure businesses of data integrity while deploying applications. For example, features like Windows Defender Application Guard help to isolate untrusted sites, ensuring a safe browsing experience for users.
Pricing is another critical factor that organizations must consider. The cost of each edition varies, with more advanced features typically associated with an increased financial commitment. However, the potential ROI through improved IT management and reduced downtime can justify these investments.
Overall, effective IT management is crucial in maximizing the potential of application deployment. Ensuring that support structures are in place will lead to seamless updates and minimize the disruption to users.
For further information on this topic, you can refer to the official Microsoft documentation: Microsoft Documentation.
In the contemporary corporate setting, remote desktop access has become a necessity for many organizations. This feature enhances business productivity by allowing employees to connect to their workstations from various locations, thus supporting flexible work arrangements.
IT management teams benefit significantly from remote desktop functionalities, enabling them to maintain and support devices without being physically present. The ability to troubleshoot issues remotely reduces downtime and improves overall system reliability.
The available remote desktop features may vary considerably between different versions of operating systems. Here are some key aspects to consider:
When evaluating these capabilities, organizations should take into account the pricing strategy for different versions of the operating system. Investing in a version that offers superior remote access features may yield a better return on investment due to increased productivity and lower operational costs.
In summary, the right choice will greatly depend on the specific needs of a business, balancing the required features against budgetary constraints and security requirements. Employers are encouraged to analyze these factors closely to foster a productive remote work environment.
For further information on remote desktop functionalities, visit Microsoft Business Solutions.
In the realm of operating systems designed for business environments, understanding support and update policies is paramount for IT management. These policies dictate how companies receive security enhancements, patches, and enterprise tools that are crucial for maintaining business productivity.
Support for business versions typically includes regular updates, which can be critical in addressing vulnerabilities and increasing system stability. Organizations need to be aware of how frequently these updates roll out and whether they come with new features or essential bug fixes.
Key aspects to consider include:
Security enhancements are another fundamental component of support policies. Businesses require timely patches to mitigate risks posed by emerging threats. Knowing how soon vulnerabilities are addressed can safeguard organizational data effectively.
When evaluating enterprise tools, it’s vital to consider how these tools are integrated within the update structure. Some solutions may require additional configuration or may only be compatible with specific updates, impacting overall workflow.
Pricing strategies for support options can also vary significantly. Budget considerations play a role in determining the level of service organizations choose. Some may opt for basic support, while others invest in premium services that offer more comprehensive coverage.
By paying close attention to support and update policies, businesses can better protect their operations, enhance productivity, and ensure that their IT infrastructure remains robust and up-to-date.