Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

In the increasingly interconnected tech landscape, the termination of valid activation codes can lead to significant challenges for individuals relying on certain applications and operating systems. Such scenarios often result in activation failure, leaving users unable to access the tools they depend upon. This sudden loss of functionality not only causes frustration but also raises concerns about potential system lockout, whereby essential features become completely unavailable.
The abrupt nature of these revocations introduces various risks that many are unprepared to handle. Individuals may find themselves facing significant disruption to their daily tasks and work, with no viable recourse for recovery. The absence of a refund policy adds salt to the wound, as consumers who have invested in these licenses may feel betrayed, having spent money on a product that has now become unusable without warning. This lack of accountability can lead to deep dissatisfaction and erode trust in the companies providing these services.
By analyzing these factors, it becomes evident that the implications of license terminations reach far beyond simple inconvenience. Consumers are often left navigating a maze of support options, seeking assistance only to be met with limited solutions. As the reliability of software resources comes into question, individuals may need to reconsider their long-term investments in such technologies, weighing the costs against the perpetuating risks of unexpected restrictions.
The revocation process serves as a critical mechanism for maintaining the integrity of licensing systems. It primarily aims to mitigate the associated risks of unauthorized use and piracy. By revoking access to a license, companies ensure that only legitimate users can access their products. If a software license is invalidated, this may lead to activation failure for those attempting to use it without proper authorization.
A common concern among users is the potential for no refund after license deactivation. The financial implications of losing access to previously acquired software can be significant for individuals and businesses alike. In many instances, users may find themselves in a predicament where they have paid for a service but are no longer able to utilize it due to license issues.
Another aspect of the process is its role in reinforcing accountability. By implementing strict revocation procedures, organizations can deter misuse and ensure that users are operating under their legal agreements. This proactive approach can support the overall functionality of software ecosystems, although it is not without drawbacks.
On one hand, effective revocation can enhance security and protect the interests of developers. On the other hand, overly aggressive measures can lead to activation failures among legitimate users, creating frustration and dissatisfaction. It is essential for companies to find a balance that protects their intellectual property while maintaining a positive relationship with their customer base.
In conclusion, grasping the intricacies of the revocation process is vital for all stakeholders. Understanding its implications can aid users in making informed decisions regarding their software purchases and usage practices. For more detailed insights, one can refer to resources available on Microsoft’s Security Blog.
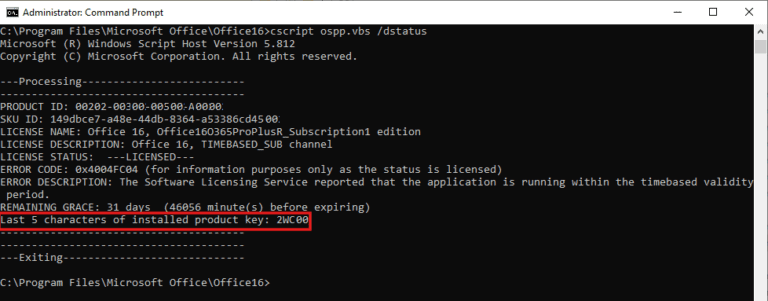
License deactivation can have significant repercussions for consumers and developers alike. The effects of this procedure extend beyond mere inconvenience; they can influence the entire software ecosystem.
When a license is deactivated, users may experience activation failure, hindering their ability to access essential features or updates. This can lead to frustration, especially for those who depend on specific applications for their daily tasks.
The implications for users can be categorized in several ways:
From a developer’s perspective, the consequences of license deactivation are equally pronounced:
In conclusion, the process of deactivating licenses creates a ripple effect across the software ecosystem. Users face barriers that can disrupt their operations, while developers may struggle with customer retention and reputational damage. Understanding these dynamics is essential for both parties to navigate the complex landscape of software licensing responsibly.
The recent revocation of certain cryptographic credentials has caused significant disruptions in the software ecosystem. Affected applications prompt system lockout messages, prevent activation, and lead to license deactivation for legitimate users. Understanding which programs are impacted is critical for users who rely heavily on specific tools for their tasks.
When software fails to authenticate due to revoked credentials, users may encounter frustrating situations. System lockout can halt productivity, forcing individuals and organizations to seek immediate resolutions. These scenarios often arise in products that require online verification, leading to activation failure and, in some cases, a complete inability to access purchased functionalities.
To aid users in identifying the affected software, it’s crucial to analyze the common characteristics of these programs. The table below lists examples of popular applications believed to be impacted by the recent credential issues:
| Application | Common Issues | Possible User Actions |
|---|---|---|
| Application A | System lockout, Activation failure | Contact support for assistance or seek an alternative |
| Application B | License deactivation, No refund | Check vendor’s policy for recovery options |
| Application C | Activation failure, System lockout | Reinstall or verify with documentation |
The consequences of activation failure and license deactivation can vary significantly. In some cases, users may find limited recourse resulting in no refunds due to the vendor’s strict policies. Complaints about unexpected fees or service interruptions have surfaced, especially among those relying on subscription-based models. Acknowledging these variables allows consumers to consider alternatives and prepare for potential challenges ahead.
This situation serves as a reminder for individuals and companies to routinely verify the status of their software licenses and stay informed about the security of the applications they utilize. As the risk of similar events looms, being proactive can help mitigate the impact on daily operations.
Receiving notifications about license changes can provoke significant concern among users of various technologies. It is important to understand the potential risks associated with such announcements, particularly regarding license deactivation and possible system lockout scenarios. Individuals should act decisively to mitigate these risks.
First, verify the authenticity of the notification. Scams can mimic legitimate notifications, leading to confusion and false alarms. Always check the source and avoid clicking on suspicious links. Authentic communications will provide clear instructions from recognized channels.
Next, review your current licenses. Understand what software you are using and the specific terms of each license agreement. Make note of expiration dates and the conditions under which deactivation may occur. This knowledge can help you stay informed about potential issues before they arise.
If your software license is at risk, consider contacting customer support immediately. Engage directly with the provider to inquire about your situation. Take note of their response and document any conversation for future reference. Be cautious, as many companies do not offer refunds once licenses are deactivated.
Another essential step is to back up your data regularly. In the event of a sudden system lockout, having your information securely saved will prevent loss. Utilize cloud storage solutions or external hard drives for added security.
Consider transitioning to licensed alternatives if you notice consistent issues with software reliability. Software that has a history of license issues may not be worth the risk. Research and compare reputable options that meet your needs while ensuring compliance with licensing regulations.
Finally, maintain a proactive approach to updates and communication from software providers. Stay informed about any changes that may affect your usage, ensuring you are always prepared and aware of your rights and obligations regarding the licenses you hold.
The deactivation of licenses poses significant security risks, leading to potential system lockout scenarios for many individuals and enterprises. When a key becomes inactive, users may find themselves unable to access crucial applications or data, resulting in operational disruptions. This situation could escalate to financial losses, particularly for businesses that rely on continuous access to specific software tools. In many cases, affected customers receive no refund after such an event, exacerbating feelings of frustration and helplessness.
On the other hand, organizations may find themselves at risk of increased vulnerabilities. When license validity is compromised, it may open doors for cybercriminals to exploit weaknesses in unprotected or outdated versions of software. Consequently, the potential for breaches grows, making it imperative for companies to assess their current circumstances and strengthen their defenses against such threats.
Protective measures must be implemented to mitigate these risks effectively. Firstly, businesses should develop a robust understanding of their software management policies. Regular audits can help ensure that all licensing agreements are current and that users are aware of the implications of license status changes. Furthermore, organizations can adopt a proactive approach by investing in service agreements that provide customer support in instances of license issues.
Additionally, maintaining an up-to-date inventory of licenses across the organization can minimize the risk of unexpected lockouts. Automated reminders for license renewals and patches help maintain access and ensure continuous functionality. Educating users on the importance of keeping software current and compliant can also be beneficial in protecting systems from potential vulnerabilities.
In conclusion, the reality of license deactivation represents a dual-edged sword. It imposes risks that can harm system access while simultaneously highlighting the necessity for proactive measures. Organizations and individuals alike should strive to minimize the potential fallout from such events by implementing sound management practices, thus fortifying their defenses against the evolving landscape of cybersecurity threats.
License deactivation can be a significant source of uncertainty for many individuals. Understanding its implications helps in clarifying common concerns that arise in this context.
What happens if my license is deactivated?
When your license is deactivated, access to the associated software may be terminated. Users often worry about the potential for system lockout, which can prevent them from utilizing their programs as intended. It’s crucial to ensure that you maintain the valid status of your license to avoid interruptions in service.
Are there risks associated with license deactivation?
Yes, there are notable risks. Deactivation can result in a loss of access to features or updates, affecting performance and security. Additionally, some programs may require reactivation, which could lead to complications, such as needing to contact support, and potentially being denied access altogether.
Will I receive a refund if my license is deactivated?
Typically, there is no refund issued for a deactivated license. This policy can leave users feeling frustrated, particularly if they encounter issues due to external factors, such as changes in software policy. It’s advisable to thoroughly review the terms of purchase to understand the implications of deactivation.
How can I prevent system lockout due to license issues?
To mitigate the chances of system lockout, keep track of your license information and renewal dates. Regularly updating your software can also help, as it often contains fixes for potential conflicts. Ensuring that payment methods are valid at the time of renewal can further safeguard against unintentional deactivation.
What support is available if I face problems with my license?
If you encounter difficulties, many companies offer customer support resources that can assist with license-related queries. Be prepared to provide pertinent information regarding your license and any troubleshooting steps you’ve already attempted. This can expedite the process of resolving your issue.
By addressing these questions and understanding the nuances related to license deactivation, users can better navigate their software experiences and minimize confusion.
The ongoing evolution of license management systems is transforming how applications are distributed and maintained. With the rise of cloud computing and online services, traditional methodologies are being reassessed. Understanding the implications of activation failures, license deactivation, and system lockout is crucial for consumers and developers alike.
Several factors highlight the challenges and opportunities in this new environment:
As digital distribution continues to expand, the balance between tight control measures and user accessibility needs careful consideration. Here are some advantages and drawbacks of current practices:
Ultimately, creating a system that balances security and user experience is critical. The transition toward more inclusive models that prioritize user satisfaction while maintaining robust protections will be essential in shaping future distribution strategies.
For ongoing updates and insights into license management trends, visit the TechRepublic.