Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

Security enhancements play a critical role in safeguarding sensitive information. As cyber threats continue to evolve, having robust protection mechanisms integrated into the software is paramount. Features that provide advanced security can differentiate between options and directly correlate with an organization’s ability to defend against breaches.
Business productivity hinges not just on tools but on the features that facilitate collaboration and workflow optimization. IT management capabilities are another key area where variances can influence how effectively systems can be integrated and maintained. Organizations must assess these distinctions to ensure they select a solution that aligns with their operational goals and team dynamics.
By carefully evaluating these elements, companies can make informed choices that promote both immediate and long-term success, leading to enhanced operational performance and security posture.
Organizations often struggle with managing devices efficiently while ensuring optimal productivity. This challenge can hinder both performance and security, leaving businesses vulnerable to various risks. Thankfully, the Professional edition offers a suite of functionalities designed to address these issues seamlessly.
One of the standout features is robust IT management. Administrators can easily deploy updates and manage configurations across multiple devices through Group Policy and Mobile Device Management (MDM). This capability provides a central point for ensuring that all systems are consistently maintained, reducing the time spent on manual updates and troubleshooting.
Business productivity is significantly enhanced with tools such as Remote Desktop and Hyper-V. Remote Desktop allows employees to access their workstations from anywhere, facilitating flexible work environments. Hyper-V, on the other hand, enables the creation of virtual machines, which can be instrumental for testing and development purposes without risking the main operating environment.
The inclusion of enterprise tools also simplifies collaboration. Features like BitLocker encryption provide a high level of data protection, ensuring that sensitive information is secure even if devices are lost or stolen. This, combined with Windows Information Protection (WIP), helps organizations mitigate the risks associated with data breaches.
Security enhancements are a priority, and this edition incorporates advanced capabilities such as Windows Defender Antivirus and Windows Defender Firewall. These built-in protections guard against malware and unauthorized access, offering peace of mind to users and IT departments alike.
In conclusion, the Professional edition is designed to tackle common issues faced by businesses through its extensive suite of features. By improving IT management, bolstering business productivity, and enhancing security measures, organizations can operate more confidently in today’s fast-paced environment.
In the realm of IT management, businesses frequently encounter challenges regarding data protection and security. As cyber threats grow more sophisticated, organizations are compelled to adopt robust measures to safeguard their vital information. Fortunately, advanced security features serve as a powerful solution to enhance protection, ensuring business productivity remains uninterrupted.
Implementing a variety of security enhancements can significantly reduce vulnerabilities while boosting overall operational efficiency. The following outlines some key options and how they can resolve common security dilemmas:
| Security Feature | Description | Benefits |
|---|---|---|
| BitLocker | A disk encryption program that secures data on drives. | Prevents unauthorized access to sensitive information. |
| Advanced Threat Protection | Detects, investigates, and responds to advanced threats. | Mitigates risks and provides a detailed threat analysis. |
| App Locker | Restricts applications that can run on devices. | Minimizes exposure to malware and boosts risk management. |
| Group Policy Management | Enables centralized control over settings and permissions. | Simplifies system configurations and enhances compliance. |
To leverage these features effectively, follow this step-by-step guide:
Step 1: Assess your organization’s specific security needs by conducting a risk assessment to identify vulnerabilities.
Step 2: Implement BitLocker on devices that handle sensitive data, ensuring that all relevant drives are encrypted for safety.
Step 3: Activate Advanced Threat Protection to monitor and respond to potential threats in real-time.
Step 4: Use App Locker to establish a whitelist of approved applications, enhancing the safety of your environment.
Step 5: Regularly review and adjust Group Policy settings to maintain appropriate access controls and compliance with security protocols.
By incorporating these advanced features into your IT infrastructure, you can not only address existing security challenges but also strengthen your defenses against future threats. This proactive approach will ultimately enhance your organization’s data security posture, ensuring business continuity and fostering a resilient work environment.
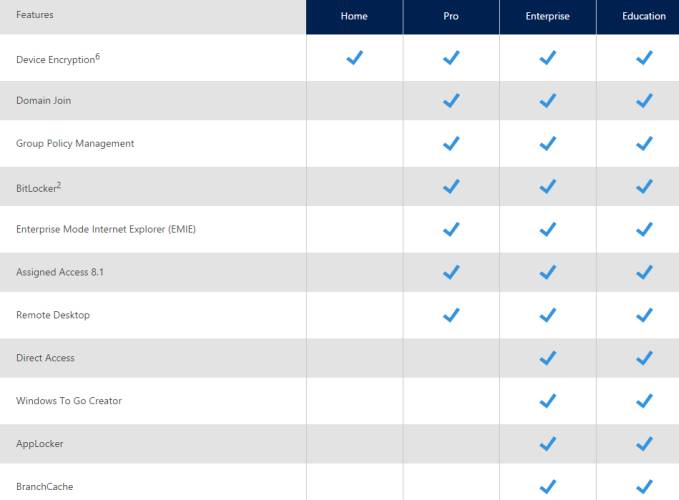
Organizations often grapple with the challenge of managing numerous devices securely and efficiently. For IT management teams, choosing the right tools can significantly impact operational effectiveness and security posture. The two editions available cater to different organizational needs, especially regarding device management functionalities.
One of the primary distinctions lies in the range of enterprise tools offered. The more advanced edition provides access to comprehensive solutions like Mobile Device Management (MDM) and Mobile Application Management (MAM), ensuring that IT teams can enforce security policies across diverse device types. This includes remote wipe capabilities, which safeguard sensitive data in the event of device loss or theft.
In comparison, the standard version may offer basic management features but lacks the robust options necessary for larger fleets of devices. While it might suffice for small businesses or individual users, growing enterprises often find it lacking as their IT environments expand.
Pricing structures also play a crucial role. The extensive management capabilities of the advanced edition come with a higher cost, reflecting the rich array of features designed for large-scale implementations. However, investing in these advanced features often leads to long-term savings by minimizing security risks and enhancing user productivity.
Security enhancements are paramount when evaluating device management options. The advanced edition includes advanced threat protection and encryption capabilities, which are indispensable for protecting sensitive organizational data. Additionally, compliance tools within this edition help organizations adhere to regulatory requirements, reducing the risk of costly fines.
To implement effective device management strategies, IT teams should consider the following steps:
Organizations can empower their IT management teams by selecting the right tools that match their specific requirements. This move not only enhances security but also streamlines operations, paving the way for a more secure digital workspace.
For further information, you can explore Microsoft’s official site.
Many small to medium businesses face challenges when it comes to virtualization capabilities required for optimizing their IT management. A common frustration arises from the lack of robust options that can effectively support business productivity. This is particularly evident when comparing different operating systems, where virtualization support, specifically Hyper-V, plays a significant role.
Identifying the right tools that align with your organization’s needs is essential for efficient IT operations. Here’s a breakdown of key aspects to consider regarding Hyper-V, primarily focusing on pricing, features, and available enterprise tools.
When evaluating options, consider the pricing structure. The Pro version is generally more affordable, making it suitable for startups and smaller teams. Conversely, the advanced option may require higher initial investment but can lead to long-term savings through improved efficiency and reduced downtime.
To decide which option fits your IT management strategy best, follow these steps:
By carefully analyzing these factors, businesses can enhance their IT management practices and select the right virtualization support that contributes positively to overall productivity and operational efficiency.

Many organizations face challenges when choosing the right operating system licensure for their needs. A common issue arises from the balance between necessary features and budgetary constraints. Businesses often need access to advanced security enhancements and improved productivity tools while remaining mindful of overall costs.
Step 1: Identify Your Needs
Begin by evaluating your organizational requirements. Consider factors such as business productivity needs, the number of employees, and the level of IT management desired. For instance, if your company handles sensitive data, investing in higher tier security features can prevent costly breaches.
Step 2: Compare Pricing Models
Review the different licensing options available. The pricing structures can vary significantly, often influenced by the scale of deployment and the specific functionalities required. For instance, solutions targeted at larger organizations typically come with additional enterprise tools which enhance management capabilities but may come with a premium price tag.
Step 3: Analyze ROI
Consider the return on investment (ROI) for different licensing choices. Assess how improvements in business productivity and centralized IT management can offset higher upfront costs. Look for features that can streamline operations and reduce time spent on administrative tasks. This may justify a higher initial cost in the long run.
Step 4: Opt for Scalable Solutions
Choose a licensing option that allows for future growth. Businesses evolve, and opting for a scalable system ensures that the investment remains viable. This adaptability can alleviate potential future costs associated with switching systems or adding licenses as your team expands.
Step 5: Stay Informed
Lastly, keep abreast of new updates and pricing changes. Software capabilities and industry standards continue to advance. Being knowledgeable about these developments enables businesses to make informed decisions, especially when assessing the need for security enhancements against the backdrop of evolving threats.
In conclusion, by methodically analyzing needs, comparing models, and considering future growth, organizations can effectively manage the licensing and cost implications associated with different operating systems. This strategic approach maximizes both security and productivity while maintaining budgetary balance.
In today’s fast-paced technological environment, maintaining robust systems can be challenging for organizations. One common issue many businesses face is the lack of timely updates and support for their software solutions. This can lead to vulnerabilities, decreased productivity, and competitive disadvantages. Fortunately, there are effective measures to enhance security and ensure that employees are equipped with the best enterprise tools available.
To tackle the problem of inadequate updates and support, businesses can adopt the following solutions:
Businesses should familiarize themselves with the update cycles associated with different software. Evaluate the frequency and types of updates provided. Key areas to consider include:
Consider purchasing support plans that offer dedicated assistance. This can ensure that your organization receives timely help when issues arise, allowing you to maintain business productivity. Look for:
Ensure that your team is well-equipped to manage the tools at their disposal. Provide regular training sessions on new features and functionalities. This can enhance:
Establish metrics to assess the effectiveness of the solutions implemented. Regularly review:
By adopting these practical solutions, organizations can not only secure their systems against potential threats but also empower their workforce to leverage modern technology effectively. Investing time in understanding update and support frameworks leads to a more resilient business model.
For more details on update and support policies, visit Microsoft Security.
Choosing the right software edition can be challenging for many organizations, especially when trying to align features with business goals. When faced with the decision between different software options, it’s crucial to assess your specific requirements and the tools that will enhance your operational capabilities.
Many companies find themselves at a crossroads between maximizing business productivity and managing costs. Before making a decision, consider the following strategies:
1. Assess Your Core Needs: Identify what features are absolutely necessary for your operations. Do you require advanced security protocols? Are collaborative tools a priority for your team? Understanding the functionalities that will elevate your workflow can guide your selection process.
2. Evaluate IT Management: Take into account the resources available for IT management. Some editions offer comprehensive management tools that simplify device configurations and updates. If your organization has limited IT support, choosing a version with robust management capabilities might save time and reduce complexity.
3. Analyze Pricing Structures: Cost plays a significant role in decision-making. Compare the pricing models of the available options, taking note of any hidden fees or long-term commitments. A more expensive edition may provide features that lead to savings in the long run, so consider the total cost versus benefits.
4. Explore Available Features: Look closely at the available features of each option. Some versions include enterprise tools that support large teams, while others focus on basic functionality. If your goal is to enhance productivity through collaboration, ensuring that the chosen software meets these expectations is essential.
5. Future-Proof Your Investment: Consider your organization’s growth potential. Choosing a solution that can scale with your needs will save you from the hassle of frequent migrations. Evaluate the capacity for upgrading or adding features as your business evolves.
By following these guidelines, you’ll be better equipped to select the edition that aligns with your organization’s goals. The right choice can lead to enhanced productivity, streamlined IT management, and overall cost-effectiveness, creating a solid foundation for your business’s success.