Physical Address
Timertau, Pr. Respubliki 19, kv 10
Physical Address
Timertau, Pr. Respubliki 19, kv 10

In an increasingly interconnected world, many users find themselves vulnerable to unexpected events that can jeopardize access to their digital resources. A common scenario arises when a license becomes inactive, leaving individuals and organizations confronting severe challenges. The ramifications include potential system lockout, loss of access to critical applications, and the frustration of dealing with no refund policies that often accompany such situations.
The risks associated with license deactivation extend beyond mere inconvenience. Organizations that invest heavily in specific software solutions may face significant disruptions in their workflow, leading to potential delays in project timelines and decreased productivity. Users are often left scrambling to regain access, identifying alternative tools or systems at a moment’s notice, which can be both time-consuming and costly.
Addressing these issues requires proactive measures. Individuals and businesses must develop a robust strategy to protect against unforeseen license cancellations. By implementing regular monitoring of license statuses and creating backup plans, users can mitigate the impact of these deactivations and ensure continuous access to essential tools without the fear of sudden interruption.
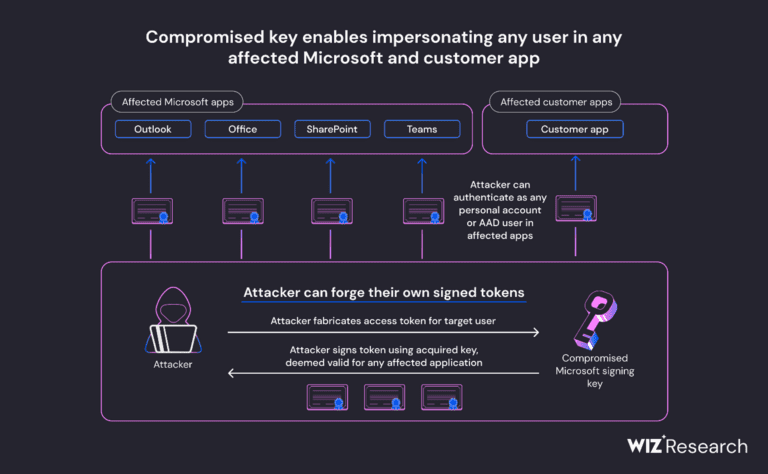
License management can present various challenges for users of software applications. A common issue arises when a program’s license becomes invalid, resulting in system lockout or activation failure. This situation can be frustrating, particularly when there is no refund option for purchased products. To navigate this obstacle, it is essential to comprehend the steps involved in the revocation of licenses in Microsoft items.
First, it is crucial to recognize that licenses can be deactivated for several reasons, including hardware changes, unapproved usage, or security breaches. Understanding these factors can help users anticipate potential issues that might lead to an unwanted cessation of service. Knowing what triggers a problem allows for proactive measures to maintain license validity.
Next, if a user suspects that a license may face deactivation, the first step should be to verify the licensing status through the product’s built-in tools. For many Microsoft applications, going to the account settings will provide clarity on the current license state. Regularly checking this information can help prevent unexpected failures and system lockout scenarios.
If problems persist, reaching out to the support team can be beneficial. Microsoft provides extensive documentation and assistance resources on their official page, offering clear guidance on how to manage licenses and troubleshoot issues. Users should not hesitate to utilize these services when necessary.
Moreover, in cases where activation fails, users can often rectify the situation by reinstalling the software or using a recovery key if available. Backing up all relevant data before a reinstall can safeguard against data loss and enable a smoother restoration process.
Lastly, maintaining a comprehensive record of all licenses, including purchase confirmations and activation codes, greatly aids in managing software rights. This documentation is invaluable in situations of license disputes or when needing assistance from support teams. By being organized, users can respond effectively to issues that arise, ultimately ensuring continued use of their software without significant interruptions.
For more detailed information, please refer to the official support website: Microsoft Support.

The sudden invalidation of a software credential can lead to significant disruptions for users. Common manifestations of this issue include activation failure and license deactivation, which can leave individuals locked out of essential applications and systems. This situation not only impacts productivity but may also lead to frustration and confusion among users trying to regain access.
When users experience system lockout, their immediate reaction may involve seeking support or troubleshooting the issue independently. However, many discover that resolving these problems can be intricate and time-consuming. In addition, users are often left with no refund for the software they cannot access, intensifying their dissatisfaction.
To mitigate these challenges, here are some practical steps that users can take:
1. Verify Activation Status: Check the software’s activation status directly within the application settings. This can often highlight whether the issue is related to a credential error.
2. Consult Official Support: Visit the official support page of the software provider. Many organizations have dedicated resources for resolving license-related issues.
3. Keep Records: Always maintain records of purchases, receipts, and activation codes. This information can be crucial when filing support requests.
4. Consider Alternatives: If access cannot be restored in a satisfactory timeframe, users should consider exploring alternative solutions or software that may provide similar functionality without activation concerns.
5. Stay Informed: Regularly check for updates or announcements from the software vendor regarding changes to licensing agreements and potential implications for users.
By taking these proactive measures, users can reduce the impact of unexpected access issues and regain control over their software environment with a clearer path forward. For more detailed information on licensing challenges and solutions, you can refer to TechRadar.
The occurrence of license deactivation can lead to significant challenges for users and organizations alike. Often, these challenges manifest as activation failure, leaving individuals locked out of systems essential for daily operations. This situation poses various risks, including lost productivity and potential data exposure.
Identifying and mitigating these pitfalls is critical. Below are key areas where vulnerabilities commonly arise and suggested approaches to address them:
| Vulnerability | Practical Solution | Benefits |
|---|---|---|
| License Deactivation | Regularly monitor license status and review notifications from vendors. | Reduces risk of unexpected service interruptions. |
| System Lockout | Implement a user-friendly recovery process that includes support resources. | Enhances user experience and minimizes downtime. |
| Activation Failure | Establish a clear protocol for handling activation issues, including escalation levels for support. | Ensures quick resolution, limiting the impact on business operations. |
| Data Exposure Risks | Conduct regular security audits to identify and address areas of vulnerability. | Strengthens overall security posture and protects sensitive information. |
By adopting these strategies, organizations can significantly reduce the adverse effects associated with license deactivation and related problems. A proactive approach fosters resilience against such disruptions while ensuring that systems remain operational and secure.
The sudden revocation of cryptographic credentials can result in significant challenges for businesses. Organizations may face system lockout, which halts operations and disrupts the workflow. Moreover, the risks associated with license deactivation can lead to financial losses and potential penalties, while the absence of refunds complicates recovery efforts.
One effective strategy for addressing the repercussions of this situation is to implement a robust backup system. Regularly back up data and maintain updated copies of software licenses to ensure minimal disruption. This proactive measure aids in restoring access should access credentials become compromised.
Another approach involves conducting regular audits of security measures. By assessing the current infrastructure and identifying potential weaknesses, businesses can enhance their resilience against unforeseen revocation incidents. Establishing a clear protocol for responding to such events is equally important, ensuring that teams know the steps to take during an emergency.
Training employees on the significance of maintaining secure practices can also mitigate risks. Providing education about the importance of managing access keys responsibly fosters a culture of vigilance within the organization. Enhanced awareness leads to proactive identification of potential issues before they escalate.
Establishing partnerships with reliable vendors can also be beneficial. By nurturing relationships with technology providers, organizations can stay informed about upcoming changes and receive timely updates that can help mitigate risks related to system lockout and license deactivation.
Finally, having a contingency fund can assist in managing unexpected costs. Allocating resources to address potential financial ramifications stemming from revocation events can provide peace of mind and facilitate smoother recovery efforts. This financial cushion enables swift action to restore operations without the burden of additional costs.
In conclusion, by implementing strategic measures such as regular backups, security audits, employee training, vendor partnerships, and financial planning, organizations can significantly alleviate the detrimental effects of key revocation events. These practices not only safeguard business operations but also enhance overall resilience against future challenges.
In various sectors, the deactivation of licenses due to unforeseen issues can lead to significant complications. One notable incident involved a major software vendor whose application faced sudden license cessation due to a certificate problem. Users experienced activation failure, leaving many without access to essential tools for ongoing projects.
This situation highlighted the risks associated with relying solely on automated systems for authentication. Many users reported frustration, especially those who had invested time and resources into the software, with no refund options available. The financial implications were particularly severe for small businesses and freelancers dependent on uninterrupted service.
Another case involved a healthcare organization whose patient management system was rendered inoperable overnight. The sudden license disruption not only halted daily operations but also compromised sensitive patient data accessibility. The aftermath showcased the vulnerability of critical infrastructures and the cascading effects on service delivery.
To address these challenges, businesses can adopt several strategies. First, implementing a robust backup plan that includes alternative software solutions can greatly mitigate risks. Organizations should also engage with vendors who provide clear communication channels and rapid support during license issues.
Key steps for prevention:
By following these practices, organizations can better shield themselves from unexpected disruptions. Ensuring a proactive approach will foster greater resilience against future software challenges, allowing teams to maintain productivity and focus on their core missions.
In complex digital environments, ensuring the validity of licensing mechanisms is paramount. A lack of monitoring tools can lead to unexpected system lockout, causing significant disruptions and potential financial loss, with no refund options available. Additionally, over-reliance on outdated methods can elevate risks, such as unauthorized software usage or license deactivation.
Here are some practical tools and strategies to effectively monitor licensing statuses:
License Management Software:
Regular Audits:
Integration with IT Asset Management:
Alerts for Expirations:
Implementing these solutions not only reduces risks associated with unauthorized access and compliance violations but also enhances overall operational stability. By proactively monitoring key statuses, organizations can minimize the chances of unexpected system lockout and ensure seamless functionality.
In the current digital environment, the challenge of managing activation codes continues to pose significant difficulties for organizations. Companies face system lockout situations that can disrupt operations, leading to potential financial losses. The deactivation of licenses without proper warning can cause frustration among users, often leaving them without support or remedies, such as no refund options, which further complicates matters.
One practical solution to prevent such issues is implementing robust key management protocols. Organizations should adopt a centralized system that allows for real-time tracking of licenses. By utilizing a management tool that integrates with existing infrastructure, businesses can minimize risks associated with sudden deactivations. This not only enhances visibility but also allows for proactive measures to be taken when a key is flagged for any reason.
Another strategy involves educating users about the importance of keeping their credentials secure. Regular training sessions on best practices for password and key management can significantly reduce the likelihood of unauthorized access, which is often the root cause of forced license revocations. Users who understand the significance of their roles in maintaining security are less likely to fall victim to phishing or other security breaches.
Furthermore, it’s essential to establish a clear contingency plan for when a license or access key is compromised. Organizations should outline precise steps for users to follow in the event of a lockout. This could include immediate access to customer support or secondary access paths while the main key is being restored or replaced. Having a well-documented procedure ensures that users know what to do and can act swiftly to reduce downtime.
In conclusion, as companies increasingly rely on cloud-based services, prioritizing effective management of access codes is paramount. By integrating advanced tracking systems, promoting user education, and establishing contingency plans, organizations can significantly enhance their resilience against license disruptions. This proactive approach not only safeguards their operations but also cultivates trust among users, ultimately leading to improved satisfaction and minimal operational interruptions.